Phyllo is now SOC 2 compliant!
On the 23rd of May, we received our final attested audit report confirming that we are now officially SOC 2 Type 2 compliant! This is in addition to the SOC 2 Type1 compliance we achieved earlier this year.
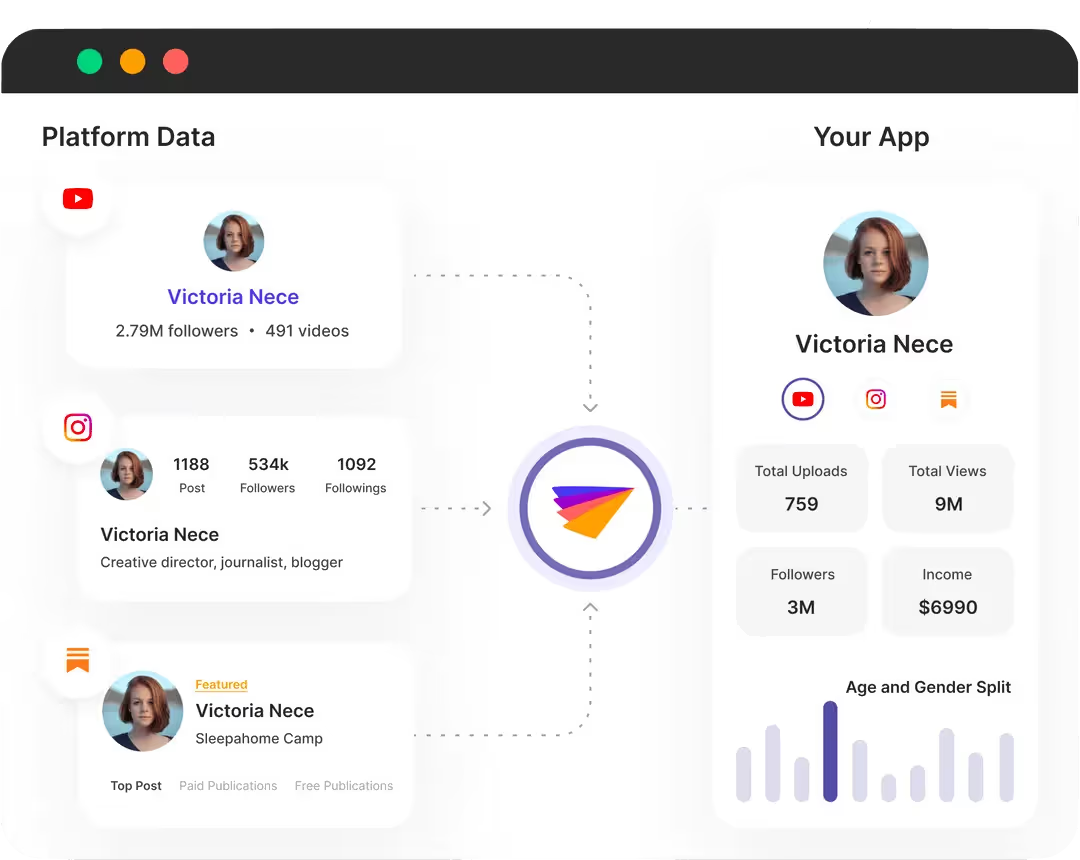
At Phyllo, we have created a data gateway that allows creator data to be accessed directly from source platforms - Instagram, TikTok, Facebook, Twitch, YouTube, and all other major social media players. We are the underlying infrastructure that connects with every creator platform, maintaining a live data feed with the connected systems.
Since we deal with customer data from all the prominent social media platforms, meeting industry standards for security and privacy is paramount for us. SOC 2 compliance is a big step towards information security by Phyllo.

What is SOC 2 compliance?
SOC 2 (Service Organization Control 2) compliance is a set of standards and guidelines developed by the American Institute of Certified Public Accountants (AICPA). It assesses and validates the security, availability, processing integrity, confidentiality, and privacy of an organization's systems and data. It is specifically designed for service organizations that handle sensitive customer data and information, such as cloud service providers, data centers, and software-as-a-service (SaaS) companies.
SOC 2 compliance is based on the Trust Services Criteria (TSC), which consists of five key principles:
- Security: The organization has implemented appropriate measures to protect its systems and data against unauthorized access, both physical and logical.
- Availability: The organization's systems and services are available and operational as agreed upon with customers, ensuring minimal downtime and disruption.
- Processing Integrity: The organization's processing systems are accurate, complete, and timely, ensuring customer data is processed correctly and reliably.
- Confidentiality: The organization maintains the confidentiality of customer information and protects it from unauthorized disclosure.
- Privacy: The organization's practices regarding the collection, use, retention, disclosure, and disposal of personal information comply with relevant privacy laws and regulations.
What is the process of SOC 2 compliance?
To achieve SOC 2 compliance, an organization undergoes an audit by an independent third-party auditor who evaluates the organization's controls, policies, and procedures against the TSC. The auditor then assesses these controls' design and operating effectiveness and issues a SOC 2 report detailing the findings.
There are two categories of SOC 2 audits:
- Type I: The report assesses a vendor's systems and determines if their design is appropriate to fulfill the applicable trust principles. It focuses on evaluating the suitability of the system's design.
- Type II: The report provides a comprehensive analysis of the operational effectiveness of those systems. It includes a historical perspective that demonstrates how controls were managed by a business over a minimum period of six months. This type of audit goes beyond design evaluation and examines controls' actual implementation and ongoing effectiveness.
The SOC 2 certification is awarded to businesses by external independent auditors upon assessing the extent to which they comply with one or more of these five trust principles:

How did Phyllo achieve SOC 2 compliance?
We started by identifying the company's service organization system and the required trust services criteria for SOC 2 compliance. Recognizing the potential complexity and time consumption involved, we explored compliance automation tools. After thorough research, we chose Sprinto, a tool that promised to streamline and enhance the efficiency of the compliance process.
With the assistance of Sprinto, our team commenced by identifying the company's service organization system and the trust services criteria mandated by SOC 2. They evaluated and tested the relevant controls to ensure effective design and operation.
Sprinto automated numerous manual compliance tasks, integrating core services like AWS, GitHub, BitBucket, Jira, and Google Workspace. It facilitated policy creation, updates, compliance status tracking, and report generation. The tool also provided real-time alerts and notifications, enabling the team to address any issues promptly.
Once all the processes were done, the Phyllo team was finally ready to have their controls assessed by an independent third-party auditor. The auditor tested the controls, determined they were operating effectively, and issued a SOC 2 report.
Why is SOC 2 compliance important for Phyllo?
The report demonstrated that Phyllo had implemented appropriate controls to protect its customers' sensitive data. The SOC 2 compliance helped Phyllo build trust with its customers and set itself as a company that takes information security seriously.
Here are some of the reasons why SOC 2 compliance is essential for growing the business of Phyllo or any tech-driven startup:
Enhanced security: Robust controls are implemented to safeguard sensitive information, reducing the risk of data breaches and unauthorized access.
Increased trust and credibility: SOC 2 certification showcases a serious commitment to security and data protection, instilling confidence among customers, partners, and stakeholders.
Compliance with industry regulations: SOC 2 helps meet specific regulations for safeguarding sensitive information and avoiding potential penalties.
Improved risk management: Identifying, assessing, and mitigating potential risks enhance an organization's ability to manage and respond to threats effectively.
Better incident response: Incident response plans are required under SOC 2, minimizing the impact of security incidents.
Enhanced vendor management: SOC 2 assesses third-party vendors' security, ensuring data protection across the supply chain.
Continuous improvement: SOC 2 compliance involves regular audits, promoting adherence to best practices, and constantly enhancing security measures.
SOC 2 compliance is increasingly becoming a norm for organizations that deal with sensitive customer data. Customers, partners, and regulators often demand it across healthcare, financial services, and technology. Organizations must validate that their systems and processes align with industry benchmarks concerning security, availability, processing integrity, confidentiality, and privacy.
Want to know more about Phyllo and our compliance process? Get in touch with us!

.avif)







